
Approx. read time: 7.5 min.
Post: Fork Bomb Batch File Virus
Fun Prank: The Fork Bomb Batch File
Want to prank your friends harmlessly? Try the Fork Bomb Batch File! It’s like a mini DDoS attack on your own system, but it won’t cause any permanent damage. Just make sure no one loses unsaved work.
The Prank
The Fork Bomb batch file creates multiple processes to consume all available system memory, eventually causing the computer to crash. It’s more annoying than harmful.
Steps to Create the Prank
- Create a Batch File: Open Notepad and copy the code below.
%0|%0
- Save the File: Save it as
RUNME.BAT(make sure it’s a.BATfile). - Run the Prank: Give it to a friend and watch the fun unfold.
Note: This prank works on Microsoft Windows Operating Systems.
Making it More Fun
To make the prank even more interesting, place the batch file on a USB stick and add an AUTORUN.INF file to automatically run the batch file when the USB is inserted into a Windows computer.
How It Works – Fork Bomb Batch File Virus
To understand the Fork Bomb batch file better, let’s break down a more detailed version of the code.
Step-by-Step Explanation
:thestart
start %0
goto thestart
- Label:
:thestart– Creates a label calledthestart. - Start Command:
start %0– Starts another instance of the batch file. - Loop:
goto thestart– Jumps back to the label, creating an infinite loop.
What Happens?
- Multiple Processes: Each process starts another, doubling the number of processes each time.
- System Overload: The computer’s memory quickly fills up, causing it to slow down and eventually crash.
Symptoms
- The machine will become sluggish.
- It might slow down significantly.
- It could halt or restart.
- Any running environment (sandbox) might terminate or restart.
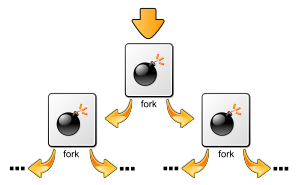
Illustration – Fork Bomb Batch File Virus
Here’s a visual representation of the Fork Bomb:

Fork Bomb Batch File Virus Illustration: Every Child Becomes A Parent Exponentially Wasting Memory.

Fork Bomb Batch File Virus Runs In Windows With Task Manager Loaded
Exponential Growth
After a few iterations, the number of processes grows exponentially:
- 1 iteration: 2 processes.
- 2 iterations: 4 processes.
- 10 iterations: 1024 processes.
- 100 iterations: 1.267 nonillion processes (10^30).
The system will crash before reaching 50 iterations.
Protection – Fork Bomb Batch File Virus
To protect against fork bombs:
- Antivirus: Most antivirus programs can detect and warn about this script.
- Limit Processes: On Linux, use the
ulimitcommand to limit the number of processes a user can create.
Example: ulimit -u 30 (limits to 30 processes).
Have fun pranking safely! Remember, it’s all in good fun, and no harm should come to anyone’s data.
Fork bomb
In computing, a fork bomb (also called rabbit virus) is a denial-of-service (DoS) attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation.
History
Around 1978, an early variant of a fork bomb called wabbit was reported to run on a System/360. It may have descended from a similar attack called RABBITS reported from 1969 on a Burroughs 5500 at the University of Washington.[1]
Implementation – Fork Bomb Batch File Virus
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table.[2][3] A basic implementation of a fork bomb is an infinite loop that repeatedly launches new copies of itself.
In Unix-like operating systems, fork bombs are generally written to use the fork system call.[3] As forked processes are also copies of the first program, once they resume execution from the next address at the frame pointer, they continue forking endlessly within their own copy of the same infinite loop; this has the effect of causing an exponential growth in processes. As modern Unix systems generally use a copy-on-write resource management technique when forking new processes,[4] a fork bomb generally will not saturate such a system's memory.
Microsoft Windows operating systems do not have an equivalent functionality to the Unix fork system call;[5] a fork bomb on such an operating system must therefore create a new process instead of forking from an existing one.
A classic example of a fork bomb is one written in Unix shell :();:, possibly dating back to 1999,[6] which can be more easily understood as
fork()
fork
In it, a function is defined (fork()) as calling itself (fork), then piping (|) its result into itself, all in a background job (&).
The code using a colon : as the function name is not valid in a shell as defined by POSIX, which only permits alphanumeric characters and underscores in function names.[7] However, its usage is allowed in GNU Bash as an extension.[8]
Prevention
As a fork bomb's mode of operation is entirely encapsulated by creating new processes, one way of preventing a fork bomb from severely affecting the entire system is to limit the maximum number of processes that a single user may own. On Linux, this can be achieved by using the ulimit utility; for example, the command ulimit -u 30 would limit the affected user to a maximum of thirty owned processes.[9] On PAM-enabled systems, this limit can also be set in /etc/security/limits.conf,[10] and on *BSD, the system administrator can put limits in /etc/login.conf.[11] Modern Linux systems also allow finer-grained fork bomb prevention through cgroups and process number (PID) controllers.[12]
See also – Fork Bomb Batch File Virus
References – Fork Bomb Batch File Virus
- ^ Raymond, Eric S. (October 1, 2004). "wabbit". The Jargon Lexicon. Archived from the original on May 15, 2012. Retrieved October 15, 2013.
- ^ Ye, Nong (2008). Secure Computer and Network Systems: Modeling, Analysis and Design. John Wiley & Sons. p. 16. ISBN 978-0470023242.
- ^ Jump up to:a b Jielin, Dong (2007). Network Dictionary. p. 200. ISBN 978-1602670006.
- ^ Dhamdhere, Dhananjay M. (2006). Operating Systems: A Concept-based Approach. McGraw-Hill Higher Education. p. 285. ISBN 0-07-061194-7.
- ^ Hammond, Mark (2000). Python Programming On Win32: Help for Windows Programmers. "O'Reilly Media, Inc.". p. 35. ISBN 1565926218.
- ^ Michal Zalewski (August 19, 1999). "[RHSA-1999:028-01] Buffer overflow in libtermcap tgetent()". Newsgroup: muc.lists.bugtraq. Retrieved December 10, 2022.
bash$ :();:} - ^ "The Open Group Base Specifications Issue 7, 2018 edition IEEE Std 1003.1™-2017 Section 3.235". The Open Group/IEEE.
Name: In the shell command language, a word consisting solely of underscores, digits, and alphabetics from the portable character set. The first character of a name is not a digit.
- ^ "The GNU Bash Reference Manual, Section 3.3". Retrieved December 11, 2022.
When the shell is in POSIX mode (see Bash POSIX Mode), fname must be a valid shell name and may not be the same as one of the special builtins (see Special Builtins). In default mode, a function name can be any unquoted shell word that does not contain '$'.
- ^ Cooper, Mendel (2005). Advanced Bash Scripting Guide. pp. 305–306. ISBN 1430319305.
- ^ Soyinka, Wale (2012). Linux Administration: A Beginners Guide. McGraw Hill Professional. pp. 364–365. ISBN 978-0071767590.
- ^ Lucas, Michael W. (2007). Absolute FreeBSD: The Complete Guide to FreeBSD. No Starch Press. pp. 198–199. ISBN 978-1593271510.
- ^ "Process Number Controller in Documentation/ as appeared in Linux kernel 5.3". October 8, 2019. Archived from the original on October 8, 2019. Retrieved October 8, 2019.
External links – Fork Bomb Batch File Virus
Related Videos:
Related Posts:
JavaScript infinite alert prank lands 13-year-old Japanese girl in hot water
Protect Your Points: The Real Cost of Email Bombing and How to Fight Back
What Are the Fundamentals and Differences Between Linux and Unix Operating Systems?
Introduction to Batch File Viruses
Exploring Islam: History, Contributions, and Dispelling Misconceptions
Coding Autorun.inf Script Virus
Introduction to Batch File Viruses











